Cybersecurity threats are virtually everywhere. The typical enterprise could be the target of threats at any time. In the fight to keep networks and applications safe, they are turning to threat intelligence platforms capable of collecting, analyzing, and creating actionable responses to threat intelligence.
Threat intelligence is easily understood through the lens of military intelligence. The idea is to continually gather as much information as possible in order to know what the enemy is up to. In cybersecurity, that’s exactly what a threat intelligence platform does.
Timeliness plays a crucial role in determining whether threat intelligence is useful. At DarkOwl, where threat intelligence is a major part of what they do, it is understood that a platform needs the ability to not only aggregate information, but also understand, anticipate, and respond to threats revealed by that information. And the response needs to be timely and effective.
Aggregating Data


Maximizing intelligence against threats is all about data. As experts explain, the goal is to gather data from as many sources as possible. Threat data is aggregated from:
- The Dark Web.
- External threat feeds.
- Open-source intelligence.
- Industry-specific threat information.
- Internal security events and logs.
Once data is aggregated, it must be normalized. This means it is transformed into a standardized format that makes it easier to analyze and correlate. Normalized data becomes a gold mine for understanding potential threats.
Data Is Analyzed and Enriched
A threat intelligence platform continues working even after data has been gathered and normalized. The platform goes on to analyze and enrich data to make it actionable. Platforms rely on advanced algorithms to:
- Correlate data points across multiple sources.
- Identify patterns and relationships pointing to threats.
- Prioritize perceived threats based on severity and relevance.
Because there are so many potential threats out there, IT teams need to prioritize. Chasing down every potential threat – especially those that present very little risk – can leave a team unable to respond to the most severe among them.
To make things easier on IT teams, a good threat intelligence platform will enrich data with context. For example, an analysis of gathered data could reveal patterns that would be enriched with geolocation information. Data can be enriched by known malicious indicators, threat actor profiles, known threat tactics, and more.
Enrichment enhances a security team’s understanding of the nature and potential impact of a perceived threat. Hearkening back to military terms, enrichment helps teams better understand the enemy’s playbook.
A Fully Integrated Threat Intelligence Platform
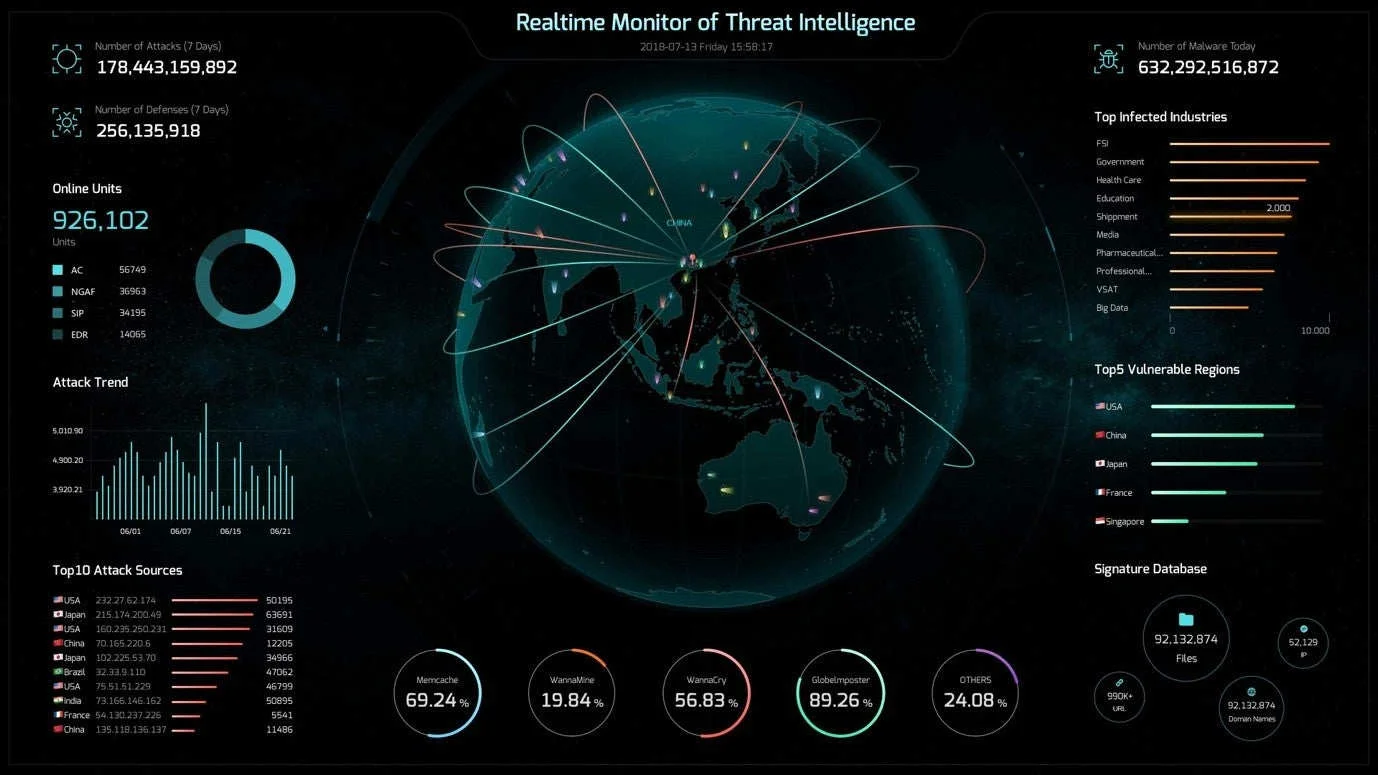

In order to maximize its capability, a threat intelligence platform should fully integrate with existing security infrastructure. For example, it should work seamlessly with a security information and event management (SIEM) system. Platforms should also integrate with:
- Firewalls (both software and hardware).
- Intrusion detection and prevention systems.
- Endpoint detection and response tools.
Integration is crucial to taking advantage of automated threat detection and response. With automation in play, IT teams can keep their attention focused on other tasks that require manual intervention. That makes for better detection and response across the entire security stack.
The Need for Actionable Intelligence
At this point, it is important to stop and consider actionable intelligence. This is a pain point for some organizations. They find themselves with so much intelligence that they don’t know what to do with it. It is possible to have too much of a good thing. It’s possible to have intelligence that does little more than pull the security team’s attention away from more important things.
One of the key reasons for implementing a threat intelligence platform is to produce actionable intelligence. This is intelligence that the IT team can actually act on in an effective and timely way. A threat intelligence platform should be able to translate raw data into:
- Customized threat feeds for different security tools.
- Customized alerts for high-priority threats.
- Accurate context for incident response.
Platforms with built-in AI are currently changing the way raw data is transformed into actionable data. As AI technologies get better, so will automated threat intelligence. Unfortunately, the other side of that coin is that threat actors are harnessing AI as well. Therefore, threat intelligence platforms need to continuously evolve to keep up with the changing landscape.
Sharing Information


The sheer size of some enterprises dictates dividing up security responsibilities among multiple teams – sometimes in different locations. Facilitating real-time communication and collaboration among them is yet another role that threat intelligence platforms play. Platforms facilitate information sharing by:
- Acting as a centralized hub for threat analysis.
- Allowing for secure threat intelligence sharing.
- Supporting industry-specific information-sharing communities (ISACs).
Always On, Always Working
The proverbial icing on the cake is that a threat intelligence platform is always on and always working. It does not need breaks throughout the day. It does not take time off, call in sick, or underperform when it is having bad days. Given what cybersecurity has become in recent years, having 24/7 protection in place is a big deal.
Thanks to continuous monitoring and adaptation, a threat intelligence platform offers:
- Realtime updates – Because a platform is continually monitoring and analyzing, it can keep IT teams informed at all times about emerging threats. IT teams can adapt more quickly and reduce the time between discovery and mitigation.
- Historical analysis – Historical analysis is often just as important as new intelligence. Therefore, a solid platform maintains a historical record of past threats, trends, and improvements in long term security solutions.
Needless to say, a threat intelligence platform significantly enhances an organization’s ability to protect itself against cybersecurity threats. A platform detects threats by aggregating data, analyzing it, and transforming it into actionable information.
If your organization is not making use of a threat intelligence platform, there is no better time than the present to change things. Cybersecurity continues to evolve. Threat actors are constantly coming up with new ways to do what they do. In order to maintain the upper hand, your organization needs the right intelligence presented in an actionable way.







